Professional Documents
Culture Documents
Equation Group - The Crow... Pionage - Kaspersky Lab
Uploaded by
Wendy Cohen0 ratings0% found this document useful (0 votes)
4 views4 pagesespionage report from kaspersky
Original Title
Equation Group_ the Crow...Pionage _ Kaspersky Lab
Copyright
© © All Rights Reserved
Available Formats
PDF or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentespionage report from kaspersky
Copyright:
© All Rights Reserved
Available Formats
Download as PDF or read online from Scribd
0 ratings0% found this document useful (0 votes)
4 views4 pagesEquation Group - The Crow... Pionage - Kaspersky Lab
Uploaded by
Wendy Cohenespionage report from kaspersky
Copyright:
© All Rights Reserved
Available Formats
Download as PDF or read online from Scribd
You are on page 1of 4
KASPERSKY2
‘Search
~ Kaspersky Inomet Sacurty - Mub.Davice
‘Goal Website
Antivirus Proto SUH Satiware
PES AT her eR voc
ALL SECURITY FOR HOME
Securiy for Business
~ Exdgot Secu Suse Adan
+ Businase Seourity Free Tial
Downloade
+ Btaed
+ Sanaa 8 SUR once Secuty E1ee‘Teal
Suey for Business
curly for Small Business
: Gigresbie
Hom a- Corporate Nows --Malwate +2018 Equation Group: The Crown Creator of Cybor-Espionage
© Comparative Tests
aa en MEDS
© Other
Aeboasts
ross Center
ortunities
gaetlvomation
+ New Zealand
Enuigtion Group: The Crown Creator of Cyber-Espionage
16 Febiassines
Vie Newel,
Fos sauetalyeats.Kespersky Lab's Global Research and Analysis Team (GReAT) has been closely monitering more than 60 advanced
threatactorsxzaponsile for cyber-attacks worldwide. The team has seen nearly everything, with attacks becoming increasingly complex
as maicAatiorestates got involved and ied to atm thomsaWves with the most advanced tools. Howover, only now Kaspersky Lab's
sxperts can confitm they have discovers a threat actor that surpasses anything known in terms of complexity and sophistication of
GE SESP EEN fs omon actin or amos vo ancades ~The Equation Group
‘RRéding to Kaspersky Lab researchers the group is unique almost in every aspect of their activities: they use tools that are very complicated
and expensive to develop, in order to infect victims, retrieve data and hide acivy in an outstandingly professional way, and ullize classic
spying techniques to deliver malicious payloads to he vicims,
To infect ther vieims, the group uses a powerlul arsenal of “implants” (Trojans) including the folowing that have been named by Kaspersky
Lab: EquationLaser, EquationDrug, DoubleFantasy, TripleFantasy, Fanny and GrayFish. Wthout a doubt there willbe other “implants” in
existence.
Equation group’s malware timeline
3001 2002 2002 2004 2005 2006 2007 2008 2009 2010 2011 2012 20132014
+ Equaondg appear the ben pled wh Grayninsomewhare im 201; enapact teeter
cnear _KAjpenfirs
WHAT MAKES THE EQUATION GROUP UNIQUE?
Utimate porsistonce and invisibility
GReAT has bean able to recover two modules which allow reprogramming ofthe hare dive firmware of more than a dezon of the popular
HDD brands. This is perhans the most powerful tool in the Equation group's arsenal and the frst known malware capable of infecting the hard
drves.
By reprogramming the hard drive firmware (rewriting the hard drive's operating system), the group achieves two purposes:
1. An extreme level of persistance that helps fo survive disk formalting and OS reinstallation. If the malware gots into the trmware, itis
available to “resurect” itself forever. It may prevent the deletion ofa certain disk sector or substitute it with a malicious one during
system boot
“Another dangerous thing is thal once the hard dive gets infected with this malicious payload, itis impossible to scan is firmware. To put
It simply: for most hard dives there are functions to write inte the hardware fimware area, but there are no functions to read it back. I
‘means that we are practically blind, and cannot detect hard drives thal have been infected by this malware” ~ wams Costin Rai, Director
of tho Global Research and Analysis Toam ai Kasporsky Lab.
2 The ability to create an invisible, persistent area hidden inside the hard dive. Itis used to save extltrated information which can be lator
retrieved by the attackers. Also in some cases it may halp the group to crack the encryption: “Taking inte account the fact that their
GrayFish implant is active from the very boot ofthe system, they have the ability to capture the encryption password and save it into this
hidden area,” explains Costin Ralu
Ability to retrieve data from isolated networks
‘The Fanny worm stands out from all the attacks performed by the Equation group. Is main purpose was to map alt-gapped networks. in other
‘words - to understand the topology of a network that cannot be reached, and to execute commands to those isolated systems. For this, it used
‘unique USB-based command and control mechanism which allowed the attackers to pass data back and forth from ai-gapped networks.
In particular, an infected USB stick with a hidden storage area was used to collect basic system information trom a computer not connected to
the Internet and to send itto the C&C when the USB stick was plugged into a computer infected by Fanny and having an Internet connection.
It the attackers wanted to run commands on the alr-gappad networks, they could save these commands Inthe hidden area of the USB stick.
\When the stick was plugged into the air-gapped comouter, Fanny recognized the commands and executed them,
Cassie spying methods to deliver malware
The attackers used un'vorsal mothods to infect targots: not only through the wob, but also in the physical world. Fr that thoy used an
Interciction technique ~ intercepting physical goods and replacing them with Trojanized versions. One such example involved targeting
participants ata scientife conference in Houston: upon returning home, some ofthe participants received a copy ofthe conference materials,
‘on a CD-ROM which was thon used to install the group's DoubleFantasy implant into the targot’s machine. The exact method by which those
(CDs were interdicted is unknown,
INFAMOUS FRIENDS: STUXNET AND FLAME
‘There are solid inks indicating that the Equation group has interacted with other powerful groups, such as the Stuxnet and Flame operators ~
generally from a position of superiority. The Equation group had access to zero-days before they were used by Stuxnet and Flame, and at
‘some point they shared exploits with others.
et
felt
Cr Burs
ex \ woe
1
For example, in 2008 Fanny used two zero-day which were introduced into Stuxnet in June 2008 and March 2010. One of those zero-days in
‘Stuxnot was actualy a Flame medile that exploits the same vulnerability and which was taken straight from the Flame platform and bul into
Stuxnet.
POWERFUL AND GEOGRAPHICALLY DISTRIBUTED INFRASTRUCTURE
The Equation group uses a vast C&C infrastructure that includes mare than 300 domairs and more than 100 servers. The servers are hosted
in multiple countries, including the US, UK. lay, Germany, Netherlands, Panama, Costa Rica, Malaysia, Colombia and Czech Republi
Kaspersky Lab is currently sinknoling a couple dozen of the 300 C&C servers.
THOUSANDS OF HIGH-PROFILE VICTIMS GLOBALLY
‘Since 2001, the Equation group has been busy infecting thousands, or perhaps even tens of thousands of vietims in more than 30 countries
‘worldwide, covaring the following sectors: Government and diplomatic institutions, Teleccmmunications, Aerospace, Energy, Nuclear
research, Oll and Gas, Miliary, Nanotechnology. Islamie activists and scholars, Mass media, Transportation, Financal institutions and
companies developing encryption technologies.
DETECTION
Kaspersky Lab observad seven exploits used by the Equation group in their malware, Atleast four of these were used as zer0-days. In
‘addiion to ths, the use of unknown exploits was observed, possibly zero-day, against Firefox 17, as used inthe Tor browser
During the infection stage, the group has the ability to use ton exploits in a chain. However Kaspersky Lab's experts observed that no mare
than threo are used: if the first one is not successful, they try with anther ane, and then withthe third one. If al three exploits fal, they don't,
infect the system.
Kaspersky Lab products detected a numberof attempis to attack its users, Many of these attacks were not successful due to Automatic Explit
Prevention tachnology which generically detects and blocks exploitation of unknown vulnerabilities. The Fanny worm, presumably compiled in
July 2008, was frst detected and blackisted by our automatic systems in December 2008,
To lea more about the Equation Group, please read the blog post avalable at Sacurolis. com.
© Kaspersky Intert Securty - Muli-Device
© Kaspersky Internat Securty 2015,
© Kaspersky AntiVius 201
Kaspersky Internat Securty for Mac
© Kaspersky Internat Securty for Androlt
© Kaspersky Password Manager
My Kaspersky New!
Compare securly products
vee Tools
Mople Products
Products tor Business
‘Kaspersky Endpoint Sacurty for Businass | Advanced
Kaspersky Endpoint Securty for Business | Select
Kaspersky Endpoint Seeurty for Businass | Core
Kaspersky Total Securly for Business
‘Targeted Seourty Solution
How to ouy / Renewal Policy
Products for Small Otfice
‘Kaspersky Small Office Security
Software Downloads
Buyonline
‘Benow lcanse
Get updates
Free tial download
Technical Support
Home product
‘Business products suppor
‘Report a suspected virus
© 1997 - 2015 Kaspersky Lab
All Rights Resorved. Industy-loading Antivirus Software
‘Silo Man
Prvacy Policy
Contact Us
Lea
You might also like
- E0-190-2008 (2) Chapter 1 PDFDocument41 pagesE0-190-2008 (2) Chapter 1 PDFWendy CohenNo ratings yet
- Mathcad Tutorial: by Colorado State University StudentDocument51 pagesMathcad Tutorial: by Colorado State University StudentDiana ScodreanuNo ratings yet
- Bancharampur Field Bore LogsDocument6 pagesBancharampur Field Bore LogsWendy CohenNo ratings yet
- Asuganj Field Bore LogsDocument5 pagesAsuganj Field Bore LogsWendy CohenNo ratings yet
- Hayashi SoilDocument8 pagesHayashi SoilWendy CohenNo ratings yet
- British standard soil and waste technical specifications guideDocument9 pagesBritish standard soil and waste technical specifications guideSagubar SathikaliNo ratings yet
- Chapter 1Document5 pagesChapter 1Wendy CohenNo ratings yet
- Analysis of Shore Pile For Deep ExcavationsDocument5 pagesAnalysis of Shore Pile For Deep ExcavationsWendy CohenNo ratings yet
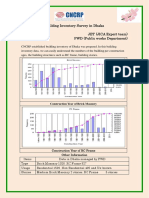
- Dhaka Building Inventory Survey Results and AnalysisDocument2 pagesDhaka Building Inventory Survey Results and AnalysisWendy CohenNo ratings yet
- Ppr12 190clrDocument23 pagesPpr12 190clrWendy CohenNo ratings yet
- Basics of Statistics: Descriptive Analysis of Birthweight DataDocument83 pagesBasics of Statistics: Descriptive Analysis of Birthweight DataMuhammad SyiardyNo ratings yet
- Design of Plumbing Systems For Multi-Storey Buildings PDFDocument14 pagesDesign of Plumbing Systems For Multi-Storey Buildings PDFpequenita34100% (4)
- Overview of Soil-Structure Interaction PrinciplesDocument58 pagesOverview of Soil-Structure Interaction PrinciplesVasco AmaralNo ratings yet
- Upvc Pressure Pipe StandardDocument4 pagesUpvc Pressure Pipe StandardTransgulf2013No ratings yet
- Bangladesh - Income Tax at A Glance - FY - 2015 - 16Document33 pagesBangladesh - Income Tax at A Glance - FY - 2015 - 16fullerineNo ratings yet
- Estimating With Microsoft ExcelDocument9 pagesEstimating With Microsoft ExcelBert EngNo ratings yet
- Universal Correlation of Shear Wave Velocity and Standard Penetration ResistanceDocument12 pagesUniversal Correlation of Shear Wave Velocity and Standard Penetration ResistanceMasayu MYusoffNo ratings yet
- Review: Preparing Journal-Format GraphsDocument5 pagesReview: Preparing Journal-Format GraphsWendy CohenNo ratings yet
- Novak ShetaDocument19 pagesNovak ShetaWendy CohenNo ratings yet
- Effect of Infill Walls On Structural FramesDocument5 pagesEffect of Infill Walls On Structural FramesWendy CohenNo ratings yet
- 1.six Sigma Basics - ArticleDocument4 pages1.six Sigma Basics - ArticleWendy CohenNo ratings yet
- ASCE Citation GuideDocument4 pagesASCE Citation GuideWendy CohenNo ratings yet
- Plagiarism, Referncing & BibliographyDocument7 pagesPlagiarism, Referncing & BibliographyWendy CohenNo ratings yet
- Techniques of Writing A Term PaperDocument7 pagesTechniques of Writing A Term PaperWendy CohenNo ratings yet
- Executive OrgansDocument19 pagesExecutive OrgansWendy CohenNo ratings yet
- An Overview: Concepts of Micro and Macro Economics: - Banik Gour SundarDocument23 pagesAn Overview: Concepts of Micro and Macro Economics: - Banik Gour SundarWendy CohenNo ratings yet
- Md. Shirajul Islam E-Mail: Approaches: Diverse ApproachDocument3 pagesMd. Shirajul Islam E-Mail: Approaches: Diverse ApproachWendy CohenNo ratings yet
- Jute Policy Revised 25 (1) .04.2011Document16 pagesJute Policy Revised 25 (1) .04.2011Wendy CohenNo ratings yet
- Power Ministry of BangladeshDocument11 pagesPower Ministry of BangladeshWendy CohenNo ratings yet
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)