Professional Documents
Culture Documents
NS - Excercise 04
Uploaded by
MikkoOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
NS - Excercise 04
Uploaded by
MikkoCopyright:
Available Formats
Assignment: Ch.
07 Firewall
Part 1: The Basics a. b. c. d. e. Define Firewall. What are the types of firewall? describe them briefly. Explain three situation when a rewall is required? To create a firewall rule there is some basic criteria that must be set. What are they? Does a rewall have to black a particular trafc both inbound (to protected site) & outbound (from protected site)? Why or why not? Which active attacks are you able to prevent by restricting access on the firewall? Note: This question presuppose you to do activity in Part 3: Simulation 2.
f.
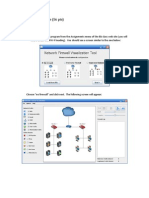
Part 2: Simulation 1 a. Install Java Runtime Environment (JRE) and run this file ftp://172.21.0.120/03%20%20Network%20Security/softwares/FirewallVisualizationTool.jar Quick Tutorial: Choose no firewall and click next. The following screen will appear:
Click the Blue PLAY button. Note that the traffic flows both from the cloud or internet to the client machines. By default, there is no malicious traffic flowing to the machines. Click on the OS Exploit option. Eventually, youll see a similar red colored bug flow from the internet into the local area network and land on a machine, infecting the machine. Once a machine is infected, it is marked as such with the international No emblem. Let us see how configuring a firewall will help prevent such infections.
b. Make a new scenario. Choose Perimeter Firewall, save as Scenario_PermitAll.dat
c. Create a rule/rules in Options Define Firewall 1 Rules to Allow all TCP and UDP traffic from cloud to 192.168.1.* and 192.168.2.*, and vice versa, make sure you ticked all the active attacks available to see whatll happen.
Part 3: Simulation 2 Download the Workstation Database scenario from ftp://172.21.0.120/03%20%20Network%20Security/softwares/Scenarios/FirewallWorkstationDataFile.dat and save it to your computer. Choose File -> new to restart the program and click load from file button, pointing the program to the file you downloaded. This scenario was configured so that workstations can pass through Firewall 2 and gain access to the database. Firewall 1 has an allow all traffic rule set so all information is passed through to the network and from the network to the servers. Write rules to prevent active attacks from passing through Firewall 1 and attacking the database.
Part 4: Submitting this Assignment Compress the .PDF file from part 1 along with .DAT files from part 2 and 3 (.zip is preferred) then upload to this site before 18/11/2013 00:00 AM.
You might also like
- Assignment 3Document5 pagesAssignment 3kevin0% (2)
- HW4 FirewallExerciseTextDocument4 pagesHW4 FirewallExerciseText'Haluk Ugurlu0% (6)
- Material Requirements Planning: Managing Inventories of Items With Dependent DemandDocument77 pagesMaterial Requirements Planning: Managing Inventories of Items With Dependent DemandYaviMansurNo ratings yet
- Agent Based Simulation of A Financial MarketDocument21 pagesAgent Based Simulation of A Financial Marketmirando93No ratings yet
- Text SummarizationDocument6 pagesText SummarizationVIVA-TECH IJRINo ratings yet
- Industrial AIDocument29 pagesIndustrial AIVipparthy Sai EsvarNo ratings yet
- Microsoft Visual Basic 6 History)Document7 pagesMicrosoft Visual Basic 6 History)Abdul Majeed Khan100% (3)
- Chapter1 PDFDocument40 pagesChapter1 PDFLuis PinuerNo ratings yet
- IQ Bot Developer Quiz Practice Q ADocument12 pagesIQ Bot Developer Quiz Practice Q AÁlvaro Andrés Quintero DíazNo ratings yet
- Safety Evaluation Process For AI Based Autonomous Systems - Pedroza - AdedjoumaDocument17 pagesSafety Evaluation Process For AI Based Autonomous Systems - Pedroza - AdedjoumaSasa VujovicNo ratings yet
- Lecture 5 - Lifecycle of A Data Science ProjectDocument55 pagesLecture 5 - Lifecycle of A Data Science ProjectGiorgio AdusoNo ratings yet
- Harmonized Tariff Schedule Rules of InterpretationDocument899 pagesHarmonized Tariff Schedule Rules of InterpretationserranovichNo ratings yet
- Lecture 8 - Lifecycle of A Data Science Project - Part 2Document43 pagesLecture 8 - Lifecycle of A Data Science Project - Part 2Giorgio AdusoNo ratings yet
- Aprilia Display Functions Cheat SheetDocument1 pageAprilia Display Functions Cheat SheetchrisgordonNo ratings yet
- Data Science CourseDocument70 pagesData Science CourseJens BaetensNo ratings yet
- HW4 FirewallExerciseTextDocument4 pagesHW4 FirewallExerciseTextAlexonNo ratings yet
- Case Study 3: FirewallDocument5 pagesCase Study 3: FirewallShrutika SutraveNo ratings yet
- Case Study 3: FirewallDocument5 pagesCase Study 3: FirewallShrutika SutraveNo ratings yet
- Assessment Task - Firewall ExerciseDocument5 pagesAssessment Task - Firewall ExerciseJoshua Nainggie0% (1)
- What Is A Firewall?Document4 pagesWhat Is A Firewall?Raja MohammedNo ratings yet
- UPC-Laboratorio - Seguridad en RedesDocument8 pagesUPC-Laboratorio - Seguridad en Redeshernan oñateNo ratings yet
- An Introduction To Checkpoint FirewallDocument14 pagesAn Introduction To Checkpoint Firewallbijaya_927622511No ratings yet
- Analyzing a Cybersecurity Exploit Using Security OnionDocument8 pagesAnalyzing a Cybersecurity Exploit Using Security OnionRahim AliNo ratings yet
- System Penetration With Metasploit Framework: Ajit Kumar PradhanDocument5 pagesSystem Penetration With Metasploit Framework: Ajit Kumar PradhanXman ReturnsNo ratings yet
- TitusElian SBACyberOps FGADTS2019 Batch2Document4 pagesTitusElian SBACyberOps FGADTS2019 Batch2Titus Elian50% (2)
- Cyb404 Module15 Lab00 Sa2775 Anne Saitejaswi PDFDocument6 pagesCyb404 Module15 Lab00 Sa2775 Anne Saitejaswi PDFSai ANo ratings yet
- IDS Troubleshooting Overview: RD RD RDDocument8 pagesIDS Troubleshooting Overview: RD RD RDhalil ibrahim soysalNo ratings yet
- Bank Soal FCNSDocument10 pagesBank Soal FCNSsaid faisalNo ratings yet
- BSC30923 - CyberSecurity Defence and Operations - CA4Document7 pagesBSC30923 - CyberSecurity Defence and Operations - CA4maheusperazzoNo ratings yet
- 2022-08-19 - Back in Black - Unlocking A LockBit 3.0 Ransomware AttackDocument6 pages2022-08-19 - Back in Black - Unlocking A LockBit 3.0 Ransomware AttackRochNo ratings yet
- HW3Document5 pagesHW3AlexonNo ratings yet
- Information and Network Security Lab: Lab Mannual FOR VII SEMESTER Computer Science & EngineeringDocument30 pagesInformation and Network Security Lab: Lab Mannual FOR VII SEMESTER Computer Science & EngineeringAnitha McNo ratings yet
- CND Prac15 (19201A0004) HarshDocument3 pagesCND Prac15 (19201A0004) Harshbarkatulla syedNo ratings yet
- CSEC630 Lab2 - IDS Revised 20110614Document18 pagesCSEC630 Lab2 - IDS Revised 20110614acg49100% (1)
- Lab7 InstructionDocument10 pagesLab7 Instructionzargham.razaNo ratings yet
- InstructiuniDocument9 pagesInstructiuni0q0No ratings yet
- CCNA Cybersecurity Operations v1.0 Skills Assessment AnswerDocument4 pagesCCNA Cybersecurity Operations v1.0 Skills Assessment Answerendang shara97% (32)
- KlsDocument5 pagesKlsNovrya Benny100% (2)
- How to Upgrade Router FirmwareDocument4 pagesHow to Upgrade Router FirmwareJorge Luis Aburdene CNo ratings yet
- Discover and Map Your Network with SolarWinds NTMDocument16 pagesDiscover and Map Your Network with SolarWinds NTMPrateik NimbalkarNo ratings yet
- PR 12Document6 pagesPR 12jivanlad22No ratings yet
- PCNSE7 - Pass Palo Alto Networks Certified Network Security Engineer ExamDocument37 pagesPCNSE7 - Pass Palo Alto Networks Certified Network Security Engineer ExamSaurabh Gupta100% (1)
- AIX HarderingDocument4 pagesAIX HarderingsvitakNo ratings yet
- Tech Note 1018 - Troubleshooting Crashes With Embedded Historian Client TrendDocument8 pagesTech Note 1018 - Troubleshooting Crashes With Embedded Historian Client Trendprofilemail8No ratings yet
- 1.5.1.1 Lab - Researching Network Attacks and Security Audit ToolsDocument4 pages1.5.1.1 Lab - Researching Network Attacks and Security Audit ToolsCharlie Nevarez Witt100% (1)
- Unit 3Document22 pagesUnit 3Ankit SinghNo ratings yet
- Troubleshooting Wonderware Application Server Bootstrap CommunicationsDocument26 pagesTroubleshooting Wonderware Application Server Bootstrap CommunicationsJoão Baptista André SabiomactetoNo ratings yet
- Placing Backdoors Through FirewallsDocument7 pagesPlacing Backdoors Through FirewallsSpyDr ByTeNo ratings yet
- Ethical Hacking Lab Setup Guide UpdatedDocument50 pagesEthical Hacking Lab Setup Guide UpdatedisaballerNo ratings yet
- FinalProject CT432 ITSecAuditsDocument49 pagesFinalProject CT432 ITSecAuditsBrian MillerNo ratings yet
- Itu Ethical Hacking Lab Setup Guide UpdatedDocument50 pagesItu Ethical Hacking Lab Setup Guide UpdatedJacobus Booysen100% (1)
- 12.1.1.7 Lab - Snort and Firewall RulesDocument9 pages12.1.1.7 Lab - Snort and Firewall RulesMuhammad TaufiqNo ratings yet
- Lab 1 Creating A Zero Trust Environment PDFDocument24 pagesLab 1 Creating A Zero Trust Environment PDFJeevan Teza YadavNo ratings yet
- Top 40 Snow Leopard security tipsDocument2 pagesTop 40 Snow Leopard security tipsJaime Andrés Suárez GaravitoNo ratings yet
- Macosx 10 6 Hardeningtips PDFDocument2 pagesMacosx 10 6 Hardeningtips PDFguard007No ratings yet
- Reversing of A Protection Scheme Based On Drivers v11 by Shub-NigurrathDocument38 pagesReversing of A Protection Scheme Based On Drivers v11 by Shub-NigurrathpepeNo ratings yet
- Cybersecurity Foundations Lab 3: Creating A Zero Trust EnvironmentDocument28 pagesCybersecurity Foundations Lab 3: Creating A Zero Trust EnvironmentJefry Gutiérrez CelisNo ratings yet
- 3e88b7ff32938bb7e2aea1e1362be9394254e0e9Document2 pages3e88b7ff32938bb7e2aea1e1362be9394254e0e9XXXNo ratings yet
- McAfee Labs Threat Advisory - Ransom-WanaCryDocument5 pagesMcAfee Labs Threat Advisory - Ransom-WanaCryIoan MaximNo ratings yet
- FireEye Endpoint Deployment Quick Start GuideDocument9 pagesFireEye Endpoint Deployment Quick Start GuideFERDYNANDUS . (00000101246)No ratings yet
- 7 - The Nature of IndustryDocument5 pages7 - The Nature of IndustryMikkoNo ratings yet
- 9 - Basic Oligopoly ModelsDocument5 pages9 - Basic Oligopoly ModelsMikkoNo ratings yet
- 8 Soal Random-FM UTS-Eks B 40a-V3 - Kunci JawabanDocument5 pages8 Soal Random-FM UTS-Eks B 40a-V3 - Kunci JawabanMikkoNo ratings yet
- Chapter 8 - Managing in Competitive, Monopolistic, and Monopolistically Competitive MarketsDocument1 pageChapter 8 - Managing in Competitive, Monopolistic, and Monopolistically Competitive MarketsMikkoNo ratings yet
- IPO Listings: Why Some Choose Nasdaq Over NYSEDocument22 pagesIPO Listings: Why Some Choose Nasdaq Over NYSEMikkoNo ratings yet
- 8 - Managing in Competitive, Monopolistic, and Monopolistically Competitive MarketsDocument6 pages8 - Managing in Competitive, Monopolistic, and Monopolistically Competitive MarketsMikkoNo ratings yet
- Chapter 9 - Basic Oligopoly ModelDocument1 pageChapter 9 - Basic Oligopoly ModelMikkoNo ratings yet
- La ConfDocument10 pagesLa ConfMikkoNo ratings yet
- Balance Sheet: INPUT DATA SECTION: Historical Data Used in The AnalysisDocument8 pagesBalance Sheet: INPUT DATA SECTION: Historical Data Used in The AnalysisMikkoNo ratings yet
- Wibisono Sukmo Wardhono, ST, MTDocument8 pagesWibisono Sukmo Wardhono, ST, MTMikkoNo ratings yet
- 3 ClientDocument1 page3 ClientMikkoNo ratings yet
- Introduction to Microcontrollers and the ATMega32 MicrocontrollerDocument46 pagesIntroduction to Microcontrollers and the ATMega32 MicrocontrollerDarrius Dela Peña100% (1)
- Cloudera Spark Developer TrainingDocument491 pagesCloudera Spark Developer TrainingNikhileshNo ratings yet
- Paper 1 - Assessment IDocument4 pagesPaper 1 - Assessment IRuchi TripathiNo ratings yet
- Rotograph D InstallationDocument31 pagesRotograph D InstallationVicenteNo ratings yet
- UE to eNB communication processDocument5 pagesUE to eNB communication processsatish mauryaNo ratings yet
- Transition To Virtualized Networks FundamentalsDocument147 pagesTransition To Virtualized Networks FundamentalsPraveen BarnwalNo ratings yet
- How To Upgrade TP-Link Wireless AC & AX RouterDocument7 pagesHow To Upgrade TP-Link Wireless AC & AX RouterStun VNNo ratings yet
- Engineered Solutions JRE DLT Rugged Military Computer SystemsDocument1 pageEngineered Solutions JRE DLT Rugged Military Computer SystemsDavid LippincottNo ratings yet
- Sync Functions Inoperative, DTC U3000-41, TSB 09-14-3 U0485, or U0100, And/Or Battery Draw With Accessory Protocol Interface Module ConnectedDocument2 pagesSync Functions Inoperative, DTC U3000-41, TSB 09-14-3 U0485, or U0100, And/Or Battery Draw With Accessory Protocol Interface Module Connectedvictor hugoNo ratings yet
- AlphaSET User Manual GBRDocument137 pagesAlphaSET User Manual GBRcostelchelariuNo ratings yet
- Anywhereusb Plus DsDocument3 pagesAnywhereusb Plus DsstevicNo ratings yet
- Mitsubishi - MF501C and MF504C Flexible Disk Drives - Installation GuideDocument2 pagesMitsubishi - MF501C and MF504C Flexible Disk Drives - Installation GuideMulyana RifkyNo ratings yet
- Module 5Document65 pagesModule 5Shilpa ShridharNo ratings yet
- CCNA 2 RIP and OSPF ConfigurationDocument8 pagesCCNA 2 RIP and OSPF ConfigurationCesar Marreroro ExpositoNo ratings yet
- All About Client Copy - Local, Remote, Import - ExportDocument25 pagesAll About Client Copy - Local, Remote, Import - Exportbarun581No ratings yet
- AutodeskProducts Pak AgusDocument8 pagesAutodeskProducts Pak AgusMariyana HarukaNo ratings yet
- Telerik Instalación WinformsDocument55 pagesTelerik Instalación WinformsAbrahan EstradaNo ratings yet
- Recorrection Cola-051935 NT 065Document76 pagesRecorrection Cola-051935 NT 065Vagish KirubaharanNo ratings yet
- Ridgeline ReferenceDocument579 pagesRidgeline ReferencedersaebaNo ratings yet
- TASK#3:: Code For ThreesumDocument8 pagesTASK#3:: Code For ThreesumMalik NaveedNo ratings yet
- Advanced Internal Oracle Tuning Techniques For SAP SystemsDocument79 pagesAdvanced Internal Oracle Tuning Techniques For SAP SystemsMarri MahipalNo ratings yet
- CISCO SAN Commands: 1.to Get Help CommandsDocument9 pagesCISCO SAN Commands: 1.to Get Help Commandsik reddyNo ratings yet
- Tle-10 Ict Quarter 1 Module 3 (Babatuan) Grade 10Document12 pagesTle-10 Ict Quarter 1 Module 3 (Babatuan) Grade 10Shua HongNo ratings yet
- Security Incident Analysis Report - 04380946Document12 pagesSecurity Incident Analysis Report - 04380946Ibrahim Khan100% (1)
- Intel Server Board S2600WT TPSDocument178 pagesIntel Server Board S2600WT TPSxelonioNo ratings yet
- A+ 220-801 and 220-802 Authorized Practice Questions Chapter 3Document19 pagesA+ 220-801 and 220-802 Authorized Practice Questions Chapter 3Squee NnyNo ratings yet
- Keyboard and Markdown Shortcuts Notion - SoDocument5 pagesKeyboard and Markdown Shortcuts Notion - SoAngel ContrerasNo ratings yet
- Our Latest Firmware Release For Ubiquiti Routers: Coova Technologies, LLCDocument8 pagesOur Latest Firmware Release For Ubiquiti Routers: Coova Technologies, LLCAmanda LewisNo ratings yet
- Data Processing InstructionsDocument21 pagesData Processing InstructionsShin chan HindiNo ratings yet
- IXOS Server PDFDocument72 pagesIXOS Server PDFKumud RanjanNo ratings yet