Professional Documents
Culture Documents
The Connection Between Security and Data & Analytics
Uploaded by
IDG_WorldCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
The Connection Between Security and Data & Analytics
Uploaded by
IDG_WorldCopyright:
Available Formats
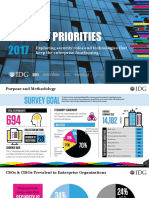
THE CONNECTION BETWEEN
SECURITY
AND
DATA & ANALYTICS
Organizations Guidelines to Securing
Data and Securing Themselves
78%
believe that the
collection & analysis
of big data has the
potential to
fundamentally
change the way
companies do business
over the next 3 years.
51%
HERES WHERE THEYRE SPENDING
57% 54% 46%
STORAGE
CAPACITY
DATA
SECURITY
23% WILL ADOPT IN THE NEXT YEAR
CLOUD
MANAGEMENT
44%
of enterprise organizations use
big data analytics to identify
information security incidents.
AN ADDITIONAL
In order to keep up with data-driven
initiatives, organizations will need to
invest in their data centers.
Security is all about
the metrics, too, and
analytics will give you
that. Youre logging it
and can quantify it. I
cant imagine doing my
job without analytics.
of organizations
expect their IT budget
allocated for data-driven
initiatives to increase
over the next 12 to 18
months.
PETER MILLER, CSO AT ORANGE COUNTY, FLORIDA,
EXPLAINED TO CSOS MICHAEL FITZGERALD
SOLVING SECURITY PROBLEMS WITH DATA
NEARLY A
The question is, do organizations value this data?
OF ORGANIZATIONS SAY
Data-Driven Initiatives Aim to Lessen Security Challenges
QUARTER (21%) THE ANSWER IS YES.
SECURITY
33%
MONITORING TOOLS
ARE A COMMON
SOURCE OF DATA
ORGANIZATIONS ARE USING DATA & ANALYTICS
TO PREPARE AGAINST THREATS.
28%
IDENTIFY COMPUTER
SECURITY RISKS
ENTERPRISE 39% SMB 29%
PREDICT FRAUD
OR FINANCIAL RISK
ENTERPRISE 32% SMB 25%
49% FINANCIAL SERVICES
Determining Security Posture Through Data & Analytics
AT THEIR ORGANIZATION.
47%
OF ORGANIZATIONS
ARE ABLE TO FEED
DATA FROM SECURITY
MONITORING ACTIVITY
INTO ANALYTICS TO
IMPROVE SECURITY
POSTURE
15%
YES,
TO GREAT EXTENT
38%
32%
OF ORGANIZATIONS
ARE CURRENTLY NOT
ABLE TO FEED DATA FROM
SECURITY MONITORING
ACTIVITY INTO ANALYTICS
TO IMPROVE SECURITY
POSTURE
18%
20%
NO, BUT WE ARE
PLANNING TO
OVER THE NEXT
12 MONTHS
NO, AND WE HAVE
NO PLANS TO
DO SO
YES,
TO SOME EXTENT
Security Ranks High in Enterprises Vendor Evaluation
51%
38%
INTEGRATION
INTO EXISTING
INFRASTRUCTURE
33%
APPROPRIATE
LEVEL OF
SCALABILITY
33%
CONFORMANCE
WITH INDUSTRY
STANDARDS
FOR SECURITY/
GOVERNANCE
SUPPORT AND SERVICES
SECURITY BEHIND THE DATA
Half of the organizations are
considering making a change to
their current information
security management model.
84%
FOR
78%
OF THEM,
THIS IS FUELED BY
CONCERNS ABOUT
DATA BREACH/
DATA LOSS
of organizations use at
least one solution to
secure the output of
their big data initiatives
What solutions are being used?
59%
52%
42%
38%
23%
IDENTITY AND ACCESS CONTROL
DATA ENCRYPTION
DATA SEGREGATION
DATA LOSS PREVENTION TOOLS
BEHAVIORAL ANALYSIS TOOLS
How sensitive really is sensitive data?
(financial information, customer information, PII, patient records)
20%
48%
HAVE PLACED
RESTRICTIONS
ON THE AMOUNT
OF SENSITIVE
DATA THEY
COLLECT
DONT EVEN COLLECT
SENSITIVE DATA
Why arent they?
NEED TO MEET COMPLIANCE MANDATES
ENTERPRISE 67% SMB 39%
Are these solutions different than
what is used to secure input data?
NO, WE FEEL THAT THE
MEASURES WE ARE
TAKING TO SECURE
EXISTING DATA OR
INPUT ARE
ADEQUATE
44%
CONCERNS ABOUT THE ABILITY TO STORE
THIS DATA IN A SECURE WAY
38%
18%
ENTERPRISE 39% SMB 36%
WE HAVE NO NEED TO COLLECT SENSITIVE DATA
YES, WE ARE TAKING
ALTERNATE OR ADDITIONAL
MEASURES TO SECURE THE
OUTPUT OF BIG DATA ONCE
ITS GENERATED
46% IT EXECUTIVES VS.
28% IT MANAGEMENT
29% IT PROFESSIONALS
35% BUSINESS MANAGEMENT
DONT KNOW
ENTERPRISE 22% SMB 46%
On a personal level:
71%
have IT Decision-Makers
changed their
SAY THEIR KNOWLEDGE OF HOW
security habits due
DATA IS USED HAS CREATED
SOME PERSONAL CONCERN
to understanding
of data?
33% HAVE LIMITED THEIR ONLINE PURCHASES AND OVERALL TECH DEVICE USAGE
37% HAVE NOT CHANGED THEIR ONLINE HABITS
29%
SAY THEIR KNOWLEDGE OF HOW
DATA IS USED HAS NOT CREATED
ANY PERSONAL CONCERN
21% DO NOT LOOK AT DATA AS A PERSONAL CONCERN
8% DO NOT HAVE ENOUGH DEVICES IN ORDER FOR COMPANIES TO TRACK THEIR DATA
SOURCES: CSOonline.com Article The CSO 2016 Security Data Analytics Survival Guide; Enterprise InfoSec CIO/Computerworld/CSO Study;
IDG Enterprise Data & Analytics Survey 2016; The 2016 Global State of Information Security Survey, in partnership with PwC, CIO, CSO, October 2015
FOR MORE INFORMATION VISIT
IDGENTERPRISE.COM/RESEARCH
You might also like
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Requester Change OrderDocument30 pagesRequester Change Ordermousabm75% (4)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Frontier Guide PDFDocument293 pagesFrontier Guide PDFmaykowlucasNo ratings yet
- Early Production Facilities PL WebDocument4 pagesEarly Production Facilities PL Webbono8950% (2)
- 2018 IDG Cloud Computing InfographicDocument1 page2018 IDG Cloud Computing InfographicIDG_WorldNo ratings yet
- CIO Tech Poll: Tech Priorities 2018Document7 pagesCIO Tech Poll: Tech Priorities 2018IDG_WorldNo ratings yet
- En-CA-1008-1 PLP-TH Transmission Product CatalogueDocument99 pagesEn-CA-1008-1 PLP-TH Transmission Product CataloguealvinNo ratings yet
- 2018 U.S. State of Cybercrime SurveyDocument9 pages2018 U.S. State of Cybercrime SurveyIDG_WorldNo ratings yet
- 2018 State of The Network InfographicDocument1 page2018 State of The Network InfographicIDG_WorldNo ratings yet
- 2018 IDG Security Priorities InfographicDocument1 page2018 IDG Security Priorities InfographicIDG_WorldNo ratings yet
- CIOs Are Driving Digital Transformation InfographicDocument1 pageCIOs Are Driving Digital Transformation InfographicIDG_WorldNo ratings yet
- 2018 CIO Tech Poll: Economic OutlookDocument8 pages2018 CIO Tech Poll: Economic OutlookIDG_World100% (1)
- 2018 IDG Security Priorities SurveyDocument9 pages2018 IDG Security Priorities SurveyIDG_WorldNo ratings yet
- IDG 2018 Cloud Computing ResearchDocument8 pagesIDG 2018 Cloud Computing ResearchIDG_World100% (4)
- 2018 IDG Digital Business SurveyDocument9 pages2018 IDG Digital Business SurveyIDG_World100% (3)
- A Guide To Understanding How Organizations Are Evolving To A Digital-First Business ModelDocument1 pageA Guide To Understanding How Organizations Are Evolving To A Digital-First Business ModelIDG_WorldNo ratings yet
- 2018 CIO Tech Poll: Economic Outlook InfographicDocument1 page2018 CIO Tech Poll: Economic Outlook InfographicIDG_WorldNo ratings yet
- State of The Network 2018Document10 pagesState of The Network 2018IDG_WorldNo ratings yet
- 2017 U.S. State of Cybercrime SurveyDocument8 pages2017 U.S. State of Cybercrime SurveyIDG_WorldNo ratings yet
- 2018 Global State of Information Security SurveyDocument9 pages2018 Global State of Information Security SurveyIDG_WorldNo ratings yet
- 2017 IDG Customer Engagement ExcerptDocument8 pages2017 IDG Customer Engagement ExcerptIDG_WorldNo ratings yet
- State of The Network 2017Document8 pagesState of The Network 2017IDG_WorldNo ratings yet
- State of The CIO 2018Document9 pagesState of The CIO 2018IDG_WorldNo ratings yet
- Digital Disruption & The NetworkDocument1 pageDigital Disruption & The NetworkIDG_WorldNo ratings yet
- IDG 2017 Security Priorities StudyDocument8 pagesIDG 2017 Security Priorities StudyIDG_WorldNo ratings yet
- 2017 CIO Tech Poll: Economic OutlookDocument6 pages2017 CIO Tech Poll: Economic OutlookIDG_WorldNo ratings yet
- State of The CIO 2017Document9 pagesState of The CIO 2017IDG_World100% (1)
- 2017 Global State of Information Security SurveyDocument7 pages2017 Global State of Information Security SurveyIDG_World100% (1)
- CSO 2016 SIEM Vendor Scorecard ResearchDocument7 pagesCSO 2016 SIEM Vendor Scorecard ResearchIDG_WorldNo ratings yet
- 2017 Customer Engagment Sample SlidesDocument8 pages2017 Customer Engagment Sample SlidesIDG_WorldNo ratings yet
- CW Forecast 2017 SampleDocument8 pagesCW Forecast 2017 SampleIDG_World100% (1)
- Demand GenerationDocument9 pagesDemand GenerationIDG_World100% (1)
- Tech Priorities 2017 SampleDocument7 pagesTech Priorities 2017 SampleIDG_WorldNo ratings yet
- Today's Cloud Focus & MotivatorsDocument1 pageToday's Cloud Focus & MotivatorsIDG_World100% (2)
- SWOT Analysis Connectivity and Digitization in German Automobile IndustryDocument12 pagesSWOT Analysis Connectivity and Digitization in German Automobile IndustryOzair ShaukatNo ratings yet
- Optional Fuel Pre Filter PARKER 16V4000Document3 pagesOptional Fuel Pre Filter PARKER 16V4000Andres HuertaNo ratings yet
- As ISO 140.6-2006 Acoustics - Measurement of Sound Insulation in Buildings and of Building Elements LaboratorDocument6 pagesAs ISO 140.6-2006 Acoustics - Measurement of Sound Insulation in Buildings and of Building Elements LaboratorSAI Global - APACNo ratings yet
- Site Observations (SO)Document3 pagesSite Observations (SO)Umar ShehzadNo ratings yet
- Innovation Catalogue: Trench DiggerDocument2 pagesInnovation Catalogue: Trench DiggerSukh SagarNo ratings yet
- Swagelok GC FittingsDocument2 pagesSwagelok GC FittingstotcsabNo ratings yet
- Wiper Seal Data Sheet A02 B 11782 1 enDocument2 pagesWiper Seal Data Sheet A02 B 11782 1 enghanNo ratings yet
- Industrial Diesel Engine: TNV DI SeriesDocument2 pagesIndustrial Diesel Engine: TNV DI SeriesJohn GarnetNo ratings yet
- Houston Area GIS Day 2009 BrochureDocument10 pagesHouston Area GIS Day 2009 BrochureTractBuilder SalesNo ratings yet
- Fender Music Instruments CorporationDocument8 pagesFender Music Instruments CorporationSarah DeanNo ratings yet
- Nuvoco launches designer concrete collection with Gauri KhanDocument2 pagesNuvoco launches designer concrete collection with Gauri Khankashyappathak01No ratings yet
- Service Wire Company - Jacketed MCDocument99 pagesService Wire Company - Jacketed MCÁrthur LimaNo ratings yet
- Cadenas PlasticasDocument530 pagesCadenas PlasticasYendrik Peluffo RiveraNo ratings yet
- Scrap Specifications CircularDocument57 pagesScrap Specifications Circulargiám địnhNo ratings yet
- Bosch PDFDocument6 pagesBosch PDFNagendra Babu NaiduNo ratings yet
- The Textile and Apparel Industry in India PDFDocument11 pagesThe Textile and Apparel Industry in India PDFhoshmaNo ratings yet
- Inhaler Brochure 2015 Concise VersionDocument40 pagesInhaler Brochure 2015 Concise VersionJan WyrwasNo ratings yet
- Spider Catalogue EXDocument36 pagesSpider Catalogue EXnindyaputri97No ratings yet
- GCD Code Dealership Name Business Manager Products Add On RemarkDocument3 pagesGCD Code Dealership Name Business Manager Products Add On RemarkSnehalNo ratings yet
- 3directional Measuring InstrumentsDocument34 pages3directional Measuring InstrumentsEmmanuel RapadaNo ratings yet
- Principle of TurbomachineryDocument159 pagesPrinciple of TurbomachinerySharath ChandraNo ratings yet
- PM and PDM EfectivenessDocument4 pagesPM and PDM Efectivenessmongej29No ratings yet
- Compact PressMaster Control System For Mechanical Stamping PressesDocument2 pagesCompact PressMaster Control System For Mechanical Stamping PressesJorge RushNo ratings yet
- Experienced BDM with proven success in business development and operations managementDocument1 pageExperienced BDM with proven success in business development and operations managementSashidhar GopalakrishnanNo ratings yet
- ASME Announces A New Certification MarkDocument2 pagesASME Announces A New Certification MarkAaron JohannigmanNo ratings yet