Professional Documents
Culture Documents
HW 2
Uploaded by
Marina CzuprynaOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
HW 2
Uploaded by
Marina CzuprynaCopyright:
Available Formats
CPS 114: Homework 2
S10
You are encouraged to type in your answers. Homework must be done individually. Due on April 19th, 2010.
1 Understanding TCP retransmission timers
TCPs computes an average round-trip time (RTT) for a connection using an exponentional weighted moving average (EWMA) estimator: srttn = RT Tn + (1 ) srttn1 rttvarn = (|RT Tn srttn1 |) + (1 ) rttvarn1 RT On = srttn + rttvarn (1) (2) (3)
where RT Tn is the nth RTT measurement, srttn is the nth estimate of RTT, rttvarn is the nth estimate of RTT variance, and RT On is the nth retransmission timeout value. In a typical TCP implementation, the parameters are set to: = 1/4, = 1/8, and = 4. Ben Bitdiddle considers this design a bit convoluted, and proposes to use a simple arithmetic average to estimate the RTT over a xed number of past samples. That is, RT T (i) ;k 0 k+1 RT On = srttn srttn =
n i=nk
(4) (5)
where k = 99, and = 2. Suppose that at time before n = 0, a TCPs RTT time is a constant 10ms. Both RTT estimates in EQ (1) and (4) converge to 10ms. At n = 0, the RTT of the TCP connection experiences a sudden change, and goes up to 1 second, and does not change afterwards. Answer the following questions: 1. With TCPs RTO estimate, whats the RTO at time when n = 1? 2. With Bens RTO estimate, whats the RTO at time when n = 1? 3. Will TCP suffer spurious (premature) retransmissions? If no, explain why. If yes, compute when the RTO estimate will be sufciently accurate to prevent spurious retransmssion. (Hint: you may want to write a small script to do this.) 4. Will Bens TCP suffer spurious (premature) retransmssion? If no, explain why. If yes, compute when the RTO estimate will be sufciently accurate to prevent spurious retransmssion.
2 Go deep with Wireshark
Wireshark http://www.wireshark.org/ is a useful tool for network trafc analysis. In this problem, you will use Wireshark to look at packet traces from a TCP connection, and answer a few questions. Log onto a linux machine ssh -X linux.cs.duke.edu, and download the tcp trace from wget http://www.cs.duke.edu/courses/spring10/cps114/labs/tcp-trace Then start Wireshark using the command wireshark tcp-trace. You may also install wireshark on your own machine, and nish the assignment there. (If you are using Ubuntu, you can use sudo apt-get install wireshark to install the package.) Answer the following questions. 1. Click on the rst packet. The window below will show you the packet details. What protocol headers are included in this packet? 2. What TCP ags are set in the rst packet? 3. What TCP options are included in the rst packet? 4. Which host does the active open? c 2010 Xiaowei Yang 1
CPS 114: Homework 2 5. Go to packet 91. Why is a Dup ACK sent? 6. Why does the sender send packet 96? 7. Go to packet 119. What might cause the sender to send this packet? 8. Go to packet 425. Which host does an active close?
S10
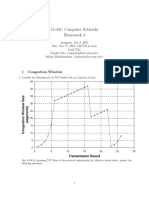
9. Go to the Statistics menu, and follow the sub-menu TCP Stream Graph. Click the Time-Sequence Graph (tcptrace). Zoom this graph so that you can see 1-second time ticks. From this graph, can you tell how many times the TCP sender does slow start, and when each slow start phase nishes? 10. What (duplicate acks or timeout) is likely to trigger the retransmission around time 2.5s? 11. What is likely to limit the senders sending window size at time 2 (cwnd, or receiver advertise window)? 12. How many packets are likely to be lost between time 2s and 7s? Circle the correct answer. A. One B. Two C. Three D. > Three
13. Around time 9.5s, another retransmssion occurs. What is likely to trigger the retransmission? 14. When does the sender receive the ACK for the packet retransmitted at around time 9.5? 15. What limits the senders sending window size at time 12s? 16. Which congestion mode is the sender in at time 13s? 17. Can you estimate the senders congestion window size at time 14s? 18. Click the Round Trip Time Graph. Can you explain why the measured RTT values uctuate so much over time from what you learned from the Time-Sequence graph? 19. Similarly, Click the Throughput Graph. Can you explain why the TCP throughput uctuates a lot between 5-10 second, but stabilizes afterwards?
3 Understanding Delay-Bandwidth Product and Router Buffer Size
20ms 1Gbps 20ms 1Mbps 20ms 1Gbps
Figure 1: A three-node network topology. Figure 1 shows a simple network topology. Node A is sending a large le to Node D using TCP. Suppose each data packets size is 1K bytes and the ACK size is 40 bytes. The initial slow start threshold ssthresh is set to a very large value (i.e., innite). To help you answer the question, we have provided you a simulation script tcp-buffer.tcl. You do not need to run the simulation to answer the following questions, but the simulation will help you understand TCP dynamics and provide hints to the answers. You may follow the instructions in the le http://www.cs. duke.edu/courses/spring10/cps114/labs/ns2-instr.txt to add the simulator to your path and run the script. 1. What is the delay-bandwidth product of this TCP connection? 2. Suppose the router B keeps a buffer size of Buf . Let Buf = 100. What is the maximum TCP congestion window size before the TCP sender suffers from a packet loss? 3. What is the TCP senders congestion window size when it detects a packet loss after three duplicate acknowledgment? c 2010 Xiaowei Yang 2
CPS 114: Homework 2 4. What is the connections RTT when router Bs buffer is full? 5. Whats the TCP connections maximum throughput?
S10
6. Can the router buffer size be reduced so that the maximum TCP throughput remains the same? If so, whats the minimal router buffer size to keep the pipe full? 7. Is it advantageous to keep a large or small buffer? What will be the optimal router buffer size in this case?
4 BGP in the wild
The Route Views project (http://www.routeviews.org/) has an archive that stores periodic BGP table dumps from several routers. Each Route Views router peers with a bunch of other routers located all over the world and receives their BGP updates in real time. So we can discover a lot about Internet routing by examining the data Route Views routers collect, or login to the routers. In this problem, we will telnet to a Route Views router and learn a bunch about its internal state. 1. Login to one of the linux cluster machines: ssh linux.cs.duke.edu. In the command line, type telnet route-views.routeviews.org 23. The rst parameter after telnet is the routers DNS name, and the second is the port we telnet into. Enter the username rviews as prompted. 2. Type ? to see the commands supported by the router. You can also type ? to complete a partial command. 3. Now run the command show ip bgp 152.3.0.0/16. The IP prex 152.3.0.0/16 is Dukes network prex. This command tells you the route advertisements the router receives from its peers. How many routes are available from this router to Duke? (The answer will be displayed at the 2nd line of the commands output.) 4. Now look at the rst route output by the command. Whats the IP address of the next hop router that advertises the route? Whats the AS path from the next hop router to Duke? Whats the local preference of the route? 5. Open another terminal, and login to linux.cs.duke.edu. Run the command traceroute -A nextHopRouter, where nextHopRouter is the IP address of the router obtained from the previous step. The -A option outputs the AS path information. What is the AS path from Duke to the next hop router? Is the path the reverse AS path from the next hop router to Duke? If not, explain why this may happen. 6. Now go back to the router login window, and scroll down until you nd the line ending with the word best. This is the best route. Whats the next hop router that advertises this best route? Whats the best AS path? Can you explain why this route is chosen as the best path?
5 Digging DNS for fun
Learn how to use dig by typing man dig on a Unix machine. Use dig to gure out the Akamai DNS server hierarchy. You may start with the domain name us.i2.yimg.com that is a customer of Akamai, and use dig to discover its Akamai canonical name, and use the +norecurse option to discover Akamai name server hierarchy. Turn in each dig commands you used and their outputs.
c 2010 Xiaowei Yang
You might also like
- CN Lab ProgramsDocument36 pagesCN Lab ProgramsKavitha SANo ratings yet
- Computer Networking Assignment HelpDocument34 pagesComputer Networking Assignment HelpComputer Network Assignment Help100% (1)
- CS 535 - Computer Networks Study Questions SolutionsDocument4 pagesCS 535 - Computer Networks Study Questions SolutionsSaurav SinghNo ratings yet
- Computer Networks FundamentalDocument7 pagesComputer Networks FundamentalThomas Kofi AnnanNo ratings yet
- Lab 2Document7 pagesLab 2claudioNo ratings yet
- Transport Layer: Computer Networking: A Top Down ApproachDocument20 pagesTransport Layer: Computer Networking: A Top Down ApproachAlamgir Ahmad KhattakNo ratings yet
- TranskateDocument7 pagesTranskateSeptian MuktiNo ratings yet
- A Review On Snoop With Rerouting in Wired Cum Wireless NetworksDocument4 pagesA Review On Snoop With Rerouting in Wired Cum Wireless NetworksInternational Organization of Scientific Research (IOSR)No ratings yet
- Lementing P Im Outing R IP Isco C CCNP: Study Guide Exam 300-101Document534 pagesLementing P Im Outing R IP Isco C CCNP: Study Guide Exam 300-101Rodrigo JuanNo ratings yet
- Practice Mid-Term SolutionDocument2 pagesPractice Mid-Term SolutionAryaman TiwariNo ratings yet
- CS45-TCP Course NotesDocument25 pagesCS45-TCP Course NotesfalconNo ratings yet
- ELEN 4017 - Network Fundamentals Tutorial No. 3: InstructionsDocument3 pagesELEN 4017 - Network Fundamentals Tutorial No. 3: Instructionsasadmehmud5934No ratings yet
- Computer Networks LabDocument15 pagesComputer Networks LabLikhith Kumar C MNo ratings yet
- Lab 03Document7 pagesLab 03Ihsan ul HaqNo ratings yet
- Assignment 1Document4 pagesAssignment 1akttripathiNo ratings yet
- Practical No.15: Theory: Tracing The Path of Website: It Involves Following StepsDocument13 pagesPractical No.15: Theory: Tracing The Path of Website: It Involves Following StepsRed Light HackersNo ratings yet
- Ext Ping TraceDocument11 pagesExt Ping TraceSandhya KumariNo ratings yet
- TCP-UDP Lab AnalysisDocument5 pagesTCP-UDP Lab Analysis徐逸明No ratings yet
- Lab3 TCPDocument7 pagesLab3 TCPAnonymous XGWa9e9iILNo ratings yet
- Datocom AnswersDocument11 pagesDatocom AnswersHalefom DestaNo ratings yet
- Vegas Re NoDocument19 pagesVegas Re NoDmytro KordubanNo ratings yet
- NS simulation implementing Large Window over TCP SACKDocument5 pagesNS simulation implementing Large Window over TCP SACKElizabeth FlowersNo ratings yet
- Comparative Analysis of TCP Variants Using NS-3.25 and Netanim On Ubuntu Version 16.04 PlatformDocument7 pagesComparative Analysis of TCP Variants Using NS-3.25 and Netanim On Ubuntu Version 16.04 PlatformIJRASETPublicationsNo ratings yet
- Computer Networks Exam, 1 TermDocument5 pagesComputer Networks Exam, 1 Termhj43usNo ratings yet
- Exercicios Kurose Ross Cap3Document8 pagesExercicios Kurose Ross Cap3Pebo GreenNo ratings yet
- CN Assignment 3 2020Document4 pagesCN Assignment 3 2020Avik DasNo ratings yet
- CCNP Routing TutorialDocument46 pagesCCNP Routing TutorialGossan AnicetNo ratings yet
- Chapter 3 - Problems - Kurose 8Document3 pagesChapter 3 - Problems - Kurose 8Luis Gomes Damasceno Neto UFCNo ratings yet
- Performance Tuning On Linux-TCPDocument6 pagesPerformance Tuning On Linux-TCPSK_shivamNo ratings yet
- TCP UDP Explained SimplyDocument11 pagesTCP UDP Explained SimplylinchiNo ratings yet
- Chapter 6 QuestionsDocument7 pagesChapter 6 Questionsahmed zuhdNo ratings yet
- TCP and Udp: by Steve Steinke, Network Magazine Feb 5, 2001 (10:03 AM)Document4 pagesTCP and Udp: by Steve Steinke, Network Magazine Feb 5, 2001 (10:03 AM)Karthick SubbiahNo ratings yet
- Feb2009 SolvedDocument4 pagesFeb2009 Solvedhj43usNo ratings yet
- ACN - Full QBDocument5 pagesACN - Full QBshabacutipieNo ratings yet
- The Source IP Address Was 192.168.102 Using Source Port 1161Document5 pagesThe Source IP Address Was 192.168.102 Using Source Port 1161Andreea PostovanNo ratings yet
- TCP Congestion Control TechniquesDocument15 pagesTCP Congestion Control TechniquesHeba Mohammed FadhilNo ratings yet
- Homework 1Document5 pagesHomework 1Aprinaldi AffandiNo ratings yet
- TCP Vegas: End To End Congestion Avoidance On A Global InternetDocument16 pagesTCP Vegas: End To End Congestion Avoidance On A Global InternetUmi UmiNo ratings yet
- Computer Networks Lab Manual: Vii SemesterDocument49 pagesComputer Networks Lab Manual: Vii SemesterGourav MehtaNo ratings yet
- Exam #1 For Computer Networks (CIS 6930) SOLUTIONS : Problem #1Document5 pagesExam #1 For Computer Networks (CIS 6930) SOLUTIONS : Problem #187bbNo ratings yet
- Lab #2: Contention-Aware Scheduling To in Wireless NetworksDocument5 pagesLab #2: Contention-Aware Scheduling To in Wireless NetworksvsalaiselvamNo ratings yet
- CN Notes-Unit VDocument5 pagesCN Notes-Unit Vapi-278882881No ratings yet
- Presentation On TCP-IP VulnerabilitiesDocument35 pagesPresentation On TCP-IP Vulnerabilitiesmohit_kohli673988% (8)
- Applying The Linear Neural Network To TCP Congestion ControlDocument5 pagesApplying The Linear Neural Network To TCP Congestion ControlEshwar DubeyNo ratings yet
- Manual For Ping (Unix/Windows NT) : Thomas Schamberg Date: 29.10.1999Document6 pagesManual For Ping (Unix/Windows NT) : Thomas Schamberg Date: 29.10.1999yudi_pasaribuNo ratings yet
- TCP Performance Evaluation using OPNETDocument6 pagesTCP Performance Evaluation using OPNETAlberto ArellanoNo ratings yet
- Chapter 2. Building Blocks of TCP: High Performance Browser NetworkingDocument13 pagesChapter 2. Building Blocks of TCP: High Performance Browser Networkingsavio77No ratings yet
- Winsock Programmer's FAQ Articles: Debugging TCP/IPDocument4 pagesWinsock Programmer's FAQ Articles: Debugging TCP/IPQ ZNo ratings yet
- Computer Networks Lab ManualDocument40 pagesComputer Networks Lab ManualAvinash Avi VNo ratings yet
- ELEN 4017 - Network Fundamentals Tutorial No. 1: InstructionsDocument3 pagesELEN 4017 - Network Fundamentals Tutorial No. 1: Instructionsasadmehmud5934No ratings yet
- Throughput Issue in Lte-DebuggingDocument6 pagesThroughput Issue in Lte-DebuggingVishal BatraNo ratings yet
- Effect of Maximum Congestion of TCP Reno in Decagon NoCDocument5 pagesEffect of Maximum Congestion of TCP Reno in Decagon NoCJournal of ComputingNo ratings yet
- Midterm F2018 SolutionDocument7 pagesMidterm F2018 SolutionSkylar WillNo ratings yet
- Midterm2 cp372 SolutionDocument8 pagesMidterm2 cp372 SolutionbottbottNo ratings yet
- MET CS 625 Business Data Communication and Networks Assignment 2Document6 pagesMET CS 625 Business Data Communication and Networks Assignment 2agalen9No ratings yet
- Assignment - 3Document8 pagesAssignment - 3Shivam SharmaNo ratings yet
- 15-441 Homework 4: TCP Congestion Control and CDNsDocument6 pages15-441 Homework 4: TCP Congestion Control and CDNsNemo CanıNo ratings yet
- ROUTING INFORMATION PROTOCOL: RIP DYNAMIC ROUTING LAB CONFIGURATIONFrom EverandROUTING INFORMATION PROTOCOL: RIP DYNAMIC ROUTING LAB CONFIGURATIONNo ratings yet
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Decibels PDFDocument4 pagesDecibels PDFMarina CzuprynaNo ratings yet
- 3GPP TS 29.303 - 23.003Document27 pages3GPP TS 29.303 - 23.003Marina CzuprynaNo ratings yet
- Inets PDFDocument85 pagesInets PDFMarina CzuprynaNo ratings yet
- Parse Tools 2.0.7 November 27 2012Document20 pagesParse Tools 2.0.7 November 27 2012Marina CzuprynaNo ratings yet
- 3GPP TS 25.427Document41 pages3GPP TS 25.427Marina CzuprynaNo ratings yet
- Parse Tools 2.0.7 November 27 2012Document20 pagesParse Tools 2.0.7 November 27 2012Marina CzuprynaNo ratings yet
- DiameterDocument48 pagesDiameterMarina CzuprynaNo ratings yet
- 3G SecurityDocument23 pages3G SecurityTaph CeesayNo ratings yet
- wns3 QemunetDocument8 pageswns3 QemunetMarina CzuprynaNo ratings yet
- Web Traffic Logs: An Imperfect Resource For EvaluationDocument11 pagesWeb Traffic Logs: An Imperfect Resource For EvaluationMarina CzuprynaNo ratings yet
- Java Client SideDocument11 pagesJava Client SideMarina CzuprynaNo ratings yet
- Full Text 01Document83 pagesFull Text 01Marina CzuprynaNo ratings yet
- Cisco ASR 920 Series Router Clocking ConfigurationDocument52 pagesCisco ASR 920 Series Router Clocking Configurationreza_azadNo ratings yet
- m120 PicDocument140 pagesm120 Picsebax123No ratings yet
- OCS DCC Interface Reference GPRS Charging ProcessDocument45 pagesOCS DCC Interface Reference GPRS Charging ProcessmikeNo ratings yet
- User Guide Intex - W300UAPDocument43 pagesUser Guide Intex - W300UAPmehul kothariNo ratings yet
- Review QuestionsDocument14 pagesReview QuestionsPaulo ParenasNo ratings yet
- Pear To Pear TechnologiesDocument15 pagesPear To Pear TechnologiesPrashant MittalNo ratings yet
- SIP5-APN-028 Time Synchronization Via IEEE 1588Document12 pagesSIP5-APN-028 Time Synchronization Via IEEE 1588erysantikaNo ratings yet
- BG-30B V11 Data Cards R1-NotesDocument13 pagesBG-30B V11 Data Cards R1-NotesmexybabyNo ratings yet
- ZXUR 9000 UMTS V4 14 10 Commissioning Guide 06 Quick Data Configuration R1 1Document151 pagesZXUR 9000 UMTS V4 14 10 Commissioning Guide 06 Quick Data Configuration R1 1nazilaNo ratings yet
- RC DS Rc3000-Sub-10fxo 10FXS 20150805 PDFDocument2 pagesRC DS Rc3000-Sub-10fxo 10FXS 20150805 PDFAgus SantosaNo ratings yet
- Interview QuestionDocument3 pagesInterview QuestionVinoth RajaguruNo ratings yet
- Chapter 18Document87 pagesChapter 18ZulaikhaEka100% (1)
- Stratix PDFDocument500 pagesStratix PDFAlan GallagherNo ratings yet
- Procedure Examples MTC RRCDocument6 pagesProcedure Examples MTC RRCShefrin MohamedNo ratings yet
- MA5600T&MA5603T&MA5608T V800R016C10 Feature Guide 02 PDFDocument2,232 pagesMA5600T&MA5603T&MA5608T V800R016C10 Feature Guide 02 PDFMonowarul Alam MonirNo ratings yet
- Ruckus RFX Template - 1Document42 pagesRuckus RFX Template - 1HendriJuniantoNo ratings yet
- Triple Carrier Layering (With Dual Carrier Full Random) : Bali IslandDocument12 pagesTriple Carrier Layering (With Dual Carrier Full Random) : Bali Islandedwin samaNo ratings yet
- Configuring PPTP (VPDN) Server On A Cisco RouterDocument7 pagesConfiguring PPTP (VPDN) Server On A Cisco RouterMaria VirginiaNo ratings yet
- FortiGate 80E SeriesDocument6 pagesFortiGate 80E SeriesAndrés HomeNo ratings yet
- Space-Time Block Coding (STBC) For Wireless NetworksDocument13 pagesSpace-Time Block Coding (STBC) For Wireless NetworksijdpsNo ratings yet
- Bahria University, Islamabad CampusDocument11 pagesBahria University, Islamabad CampusTayyab RafiqueNo ratings yet
- Learning Activity Sheet In: Computer Systems ServicingDocument12 pagesLearning Activity Sheet In: Computer Systems ServicingCarvalds 0315No ratings yet
- Telenor 2Document27 pagesTelenor 2Ali HashmiNo ratings yet
- Network Migration Strategies IJERTV3IS110835Document5 pagesNetwork Migration Strategies IJERTV3IS110835Raj VaradhNo ratings yet
- Mikrotik MTCNA Basix Certification Sample TestDocument7 pagesMikrotik MTCNA Basix Certification Sample TestMarco Antonio Urquiola RivasNo ratings yet
- 166 0918 Certificate IADS Tetra-System-R8 TSep STP9000 v1Document24 pages166 0918 Certificate IADS Tetra-System-R8 TSep STP9000 v1Luciano AraujoNo ratings yet
- CCNA Discovery 4 - Module 4 Exam Answers Version 4.0Document7 pagesCCNA Discovery 4 - Module 4 Exam Answers Version 4.0haider-rnd75% (4)
- Billing ConceptsDocument50 pagesBilling ConceptsShalini Kumari100% (1)
- Overview of LTE Physical LayerDocument13 pagesOverview of LTE Physical LayerRamy .. MarianNo ratings yet
- 2 Ruggedcom Switch RSG2488 DatasheetDocument7 pages2 Ruggedcom Switch RSG2488 DatasheetBalakrishnan KrishnanNo ratings yet