Professional Documents
Culture Documents
Creacion VPN IPSEC
Uploaded by
Carlos Amaranti GonzálezOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Creacion VPN IPSEC
Uploaded by
Carlos Amaranti GonzálezCopyright:
Available Formats
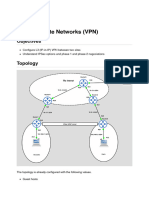
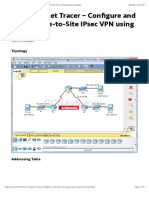
Elegir esp o ah (protocol IPSec) 1.- IPsec VPN Settings on R1 and R3 1.1.
- Habilitar las polticas IKE en cada router R1(config)#crypto isakmp enable R1(config)#crypto isakmp policy 10 1.2.- Configurar los parmetros de las polticas ISAKMP en R1 y en R3 R1(config)#crypto isakmp policy 10 R1(config-isakmp)#authentication pre-share R1(config-isakmp)#encryption aes 256 R1(config-isakmp)#hash sha R1(config-isakmp)#group 5 R1(config-isakmp)#lifetime 3600 R1(config-isakmp)#end 1.3.- Configurar las key pre-shared R1(config)#crypto isakmp key <clave compartida > address <ip publica peer > R3(config)#crypto isakmp key <clave compartida> address < ip publica peer > 1.4.- Configurar la transformada IPSec y los tiempos de vida R1(config)#crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac R1(cfg-crypto-trans)#exit R1(config)#crypto ipsec security-association lifetime seconds 1800 1.5.- Definir trfico interesante R1(config)#access-list 101 permit ip <red interna VPN> <wildcard> <red destino VPN> <wildcard> R3(config)#access-list 101 permit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255 1.6.- Crear y aplicar un crypto map R1(config)#crypto map CMAP 10 ipsec-isakmp R1(config-crypto-map)#match address 101 R1(config-crypto-map)#set peer 10.2.2.1/ IP PUBLICA DESTINO R1(config-crypto-map)#set pfs group5 / idem definido en policy 10 R1(config-crypto-map)#set transform-set 50 / mismo nombre transformada R1(config-crypto-map)#set security-association lifetime seconds 900 R1(config-crypto-map)#exit R1(config)#interface S0/0/0 interfaz conectada a red publica R1(config-if)#crypto map CMAP / asocial con crypto map creado 2.- Verificar la configuracin de la VPN IPSec Site-to-Site. R1#show crypto ipsec transform-set Transform set 50: { esp-256-aes esp-sha-hmac } will negotiate = { Tunnel, }, R1#show crypto map Crypto Map "CMAP" 10 ipsec-isakmp Peer = 10.2.2.1 Extended IP access list 101 access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 Current peer: 10.2.2.1 Security association lifetime: 4608000 kilobytes/900 seconds PFS (Y/N): Y DH group: group5 Transform sets={
50: { esp-256-aes esp-sha-hmac } , } Interfaces using crypto map MYMAP: Serial0/0/0 3.- Verificar la operacin de la VPN IPSec R1#show crypto isakmp sa dst src state conn-id slot status R1#show crypto ipsec sa interface: Serial0/0/0 Crypto map tag: CMAP, local addr 10.1.1.1 protected vrf: (none) local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0) current_peer 10.2.2.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 10.1.1.1, remote crypto endpt.: 10.2.2.1 path mtu 1500, ip mtu 1500, ip mtu idb Serial0/0/0 current outbound spi: 0x0(0) inbound esp sas: inbound ah sas: inbound pcp sas: outbound esp sas: outbound ah sas: outbound pcp sas:
4.- Configurar el tunel GRE R1(config)# interface tunnel 0 R1(config-if)# ip address ip y mascara asignada. R1(config-if)# tunnel source <nombre int conectada al tunel > R1(config-if)# tunnel destination <ip publica destino tunel> R3(config)# interface tunnel0 R3(config-if)# ip address 172.16.13.3 255.255.255.0 R3(config-if)# tunnel source serial0/0/1 R3(config-if)# tunnel destination 192.168.12.1
tipo de transformada AH
IOS transform ah-md5-hmac AH-sha-hmac Esp-aes Esp-aes 192
descripcin AH con autenticacin MD5 AH con autenticacin SHA ESP con encriptacin AES 128 ESP con encriptacin AES 192 ESP con encriptacin AES 256 ESP con encriptacin DES 56 ESP con encriptacin des 168 ESP con autenticacin MD5 ESP con autenticacin SHA
ESP encriptacion
Esp-aes 256 Esp-des Esp-3des
ESP autenticacion
ESP-sha-hmac ESP-md5-hmac
You might also like
- Configuration On Router1 Set Isakmp Policy Enable (Site To Site VPN)Document7 pagesConfiguration On Router1 Set Isakmp Policy Enable (Site To Site VPN)Varun MalhotraNo ratings yet
- Lab Cisco VPN-GenericDocument2 pagesLab Cisco VPN-Genericbliss21100% (5)
- Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument6 pagesConfigure and Verify A Site-To-Site IPsec VPN Using CLIMilošKovačevićNo ratings yet
- Config VPNDocument28 pagesConfig VPNAureo Miraval BravoNo ratings yet
- IPSec VPNDocument5 pagesIPSec VPNcciersmanNo ratings yet
- Ipsec ConfigurationDocument12 pagesIpsec Configurationharshit asharaNo ratings yet
- Technical ReportDocument19 pagesTechnical ReportUsmanNo ratings yet
- VPN Site To Site Packet Tracer 5Document2 pagesVPN Site To Site Packet Tracer 5R.s. FélixNo ratings yet
- TP4'-Ipsec VPN Site To SiteDocument2 pagesTP4'-Ipsec VPN Site To SiteGeraud TchadaNo ratings yet
- TP4'-Ipsec VPN Site To SiteDocument2 pagesTP4'-Ipsec VPN Site To SiteGERAUDNo ratings yet
- 8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLIDocument5 pages8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLITalha Ur RehmanNo ratings yet
- 8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorDocument5 pages8.7.1.4 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLI - InstructorSalem TrabelsiNo ratings yet
- Configure and Verify A Site To Site IPsec VPN Using CLIDocument4 pagesConfigure and Verify A Site To Site IPsec VPN Using CLICristhian HadesNo ratings yet
- IPSec VPN LABDocument7 pagesIPSec VPN LABAparna Garg100% (2)
- IPsec quick and dirtyDocument4 pagesIPsec quick and dirtysgopal7No ratings yet
- Lab VPNDocument9 pagesLab VPNhung kungNo ratings yet
- Yasser Auda CCIEv5 WorkbookDocument26 pagesYasser Auda CCIEv5 WorkbookphamvanhaNo ratings yet
- S2S Ikev2 Configure-AsaDocument9 pagesS2S Ikev2 Configure-Asahesenzade38No ratings yet
- Manual Lab 3Document6 pagesManual Lab 3nunezbarbakatherinerominaNo ratings yet
- BGP Over IPSEC. (Underlay IPSEC and Overlay BGP)Document4 pagesBGP Over IPSEC. (Underlay IPSEC and Overlay BGP)hamzakilameNo ratings yet
- ISP Lab Tutorial - GNS3Document19 pagesISP Lab Tutorial - GNS3Ceh0% (1)
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument4 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarNo ratings yet
- Part 1: Configure Ipsec Parameters On R1: Version CommandDocument3 pagesPart 1: Configure Ipsec Parameters On R1: Version CommandArun TSNo ratings yet
- Lan2lan VPNDocument6 pagesLan2lan VPNFelix BlasioNo ratings yet
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDocument6 pagesConfiguring Site To Site IPSec VPN Tunnel Between Cisco Routerskymk21No ratings yet
- Cisco Show CommandsDocument20 pagesCisco Show CommandsNorbert OngNo ratings yet
- Ticket 9 - DMVPNDocument9 pagesTicket 9 - DMVPNPeter HixNo ratings yet
- Configuring Site To Site Ipsec VPN Tunnel Between Cisco RoutersDocument6 pagesConfiguring Site To Site Ipsec VPN Tunnel Between Cisco RoutersSyed AliNo ratings yet
- TP-1 VPN Configuration Lab Using Routers in Cisco Packet TracerDocument5 pagesTP-1 VPN Configuration Lab Using Routers in Cisco Packet TracerKhaoula RAZZAKINo ratings yet
- 16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersDocument6 pages16.2.2 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ITExamAnswersimen loussaiefNo ratings yet
- 19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersDocument5 pages19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersAna Maria Citlali Diaz HernandezNo ratings yet
- ISAKMP RSA key IPsec tunnelsDocument4 pagesISAKMP RSA key IPsec tunnelssgopal7No ratings yet
- Gre Over Ipsec VPN: Lab TopologyDocument8 pagesGre Over Ipsec VPN: Lab TopologyyasserNo ratings yet
- Ipsec VPN Requirements: Configure Isakmp (Ike) - (Isakmp Phase 1)Document4 pagesIpsec VPN Requirements: Configure Isakmp (Ike) - (Isakmp Phase 1)Om PuriNo ratings yet
- Lab EIGRP 2Document15 pagesLab EIGRP 2Danny Ricce EnriqueNo ratings yet
- Day3 Ch2 Manag IOSDocument27 pagesDay3 Ch2 Manag IOSManoj BorahNo ratings yet
- CCNA Exploration 2 Init configuration and Cisco Discovery Protocol (CDPDocument8 pagesCCNA Exploration 2 Init configuration and Cisco Discovery Protocol (CDPamjikbookNo ratings yet
- SDWAN Ipsec IKEV2Document2 pagesSDWAN Ipsec IKEV2piyush aggarwalNo ratings yet
- LAB RPT Site-Site IPSecDocument11 pagesLAB RPT Site-Site IPSecv4meetNo ratings yet
- Site to Site VPN CLI Setup on GNS3Document6 pagesSite to Site VPN CLI Setup on GNS3dayno_majNo ratings yet
- 4.1 4-S2S-IPSecVPN-Tunnel-RouterDocument6 pages4.1 4-S2S-IPSecVPN-Tunnel-Routeramit_post2000No ratings yet
- Lab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysDocument6 pagesLab 13.8.1 Configuring A Site-To-Site Ipsec VPN Using Pre-Shared KeysKishore Reddy KandiNo ratings yet
- EIGRP LAB TrickDocument20 pagesEIGRP LAB Trickziad Al-showaiterNo ratings yet
- Router Vpnclient Pi StickDocument10 pagesRouter Vpnclient Pi Stickjames SpywangNo ratings yet
- InteropDocument6 pagesInteropSaurav LodhNo ratings yet
- Ccna Commande 3Document5 pagesCcna Commande 3شيماء عياشيNo ratings yet
- IpsecDocument10 pagesIpsecHatem KhadhraouiNo ratings yet
- Configuring Point-To-Point GRE VPN Tunnels - Unprotected GRE & Protected GRE Over IPSec TunnelsDocument7 pagesConfiguring Point-To-Point GRE VPN Tunnels - Unprotected GRE & Protected GRE Over IPSec Tunnelsst_kannanNo ratings yet
- Apuntes CCNA SecurityDocument7 pagesApuntes CCNA SecuritySantiago Balaguer GarcíaNo ratings yet
- Configure and Verify Site-to-Site IPsec VPNDocument8 pagesConfigure and Verify Site-to-Site IPsec VPNAkram AliNo ratings yet
- Lab3 IPSecDocument13 pagesLab3 IPSecDanarNo ratings yet
- 20.2.1 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ILMDocument6 pages20.2.1 Packet Tracer - Configure and Verify A Site-to-Site IPsec VPN Using CLI - ILMandres.fantinNo ratings yet
- Network Security LabsDocument13 pagesNetwork Security Labssaadalsamed2020No ratings yet
- Router 1: Router 3:: ! (Basic Configuration For Connection To Internet) ! (Basic Configuration For Connection To Internet)Document6 pagesRouter 1: Router 3:: ! (Basic Configuration For Connection To Internet) ! (Basic Configuration For Connection To Internet)tester testerNo ratings yet
- Cisco Ipsec Static DynamicDocument9 pagesCisco Ipsec Static DynamichsitadmNo ratings yet
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDocument9 pagesConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriNo ratings yet
- Routing Authentication and Passive InterfacesDocument3 pagesRouting Authentication and Passive Interfacesshimaa ashrafNo ratings yet
- Configure ASA device and site-to-site IPsec VPNDocument13 pagesConfigure ASA device and site-to-site IPsec VPNDavid VardanyanNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Infineon-Future Requirements For Automotive Hardware Security-Whitepaper-V01 00-ENDocument18 pagesInfineon-Future Requirements For Automotive Hardware Security-Whitepaper-V01 00-ENRavindra BNo ratings yet
- On The Design Details of SS/PBCH, Signal Generation and PRACH in 5G-NRDocument21 pagesOn The Design Details of SS/PBCH, Signal Generation and PRACH in 5G-NRSukshith ShettyNo ratings yet
- OR 6205 DETERMINISTIC OPERATIONS RESEARCH CLASS PACKETDocument137 pagesOR 6205 DETERMINISTIC OPERATIONS RESEARCH CLASS PACKETHari PalaniswamyNo ratings yet
- Purvanchal Vidyut Vitaram Nigam LTDDocument1 pagePurvanchal Vidyut Vitaram Nigam LTDVIKAS MISHRANo ratings yet
- Administration Guide Open Bee Sync (En)Document36 pagesAdministration Guide Open Bee Sync (En)peka76No ratings yet
- WDT V100R005C00SPC100 Propaganda Slides For Indonesia 201501Document56 pagesWDT V100R005C00SPC100 Propaganda Slides For Indonesia 201501Ronie MarxistNo ratings yet
- MSP430 C Compiler Programming GuideDocument242 pagesMSP430 C Compiler Programming Guidecharles_sieNo ratings yet
- SNMP Tutorial Explains Manager/Agent ModelDocument6 pagesSNMP Tutorial Explains Manager/Agent ModelcmohimacNo ratings yet
- Contactores1 PDFDocument52 pagesContactores1 PDFHenry ManzanedaNo ratings yet
- Accessing SQLite Databases in PHP Using PDODocument3 pagesAccessing SQLite Databases in PHP Using PDOPedro Boanerges Paz RomeroNo ratings yet
- HA16129FPJ Datasheet 1Document24 pagesHA16129FPJ Datasheet 1Dylan FlorezNo ratings yet
- Core Banking Solutions FinalDocument7 pagesCore Banking Solutions FinalShashank VarmaNo ratings yet
- Atlas Systems OverviewDocument8 pagesAtlas Systems OverviewJoaquin Manuel Macias MartinezNo ratings yet
- Job PostingDocument1 pageJob Postingjames curcioNo ratings yet
- How To Find Oracle Database Patches InstalledDocument2 pagesHow To Find Oracle Database Patches InstalledAnonymous 8RhRm6Eo7hNo ratings yet
- Public Key Infrastructure 101Document130 pagesPublic Key Infrastructure 101Robin RohitNo ratings yet
- Install ESX Server 3.5 GuideDocument24 pagesInstall ESX Server 3.5 GuideKarimulla KolimiNo ratings yet
- hMailServer Configuration GuideDocument7 pageshMailServer Configuration GuideTvshows You MissedNo ratings yet
- Kelompok 13 (Writing An Absract)Document6 pagesKelompok 13 (Writing An Absract)Muharam sanitarianNo ratings yet
- PCM 1718Document14 pagesPCM 1718isaiasvaNo ratings yet
- Sample Paper PVTC: Building Standards in Educational and Professional TestingDocument7 pagesSample Paper PVTC: Building Standards in Educational and Professional Testingsamey21No ratings yet
- LOEWE Certos Service ManualDocument79 pagesLOEWE Certos Service Manualroberto100% (6)
- Manual Bms8n2 e LowDocument58 pagesManual Bms8n2 e Lowzoranbt80_324037655No ratings yet
- Database exam questions and answers from Arid Agriculture UniversityDocument3 pagesDatabase exam questions and answers from Arid Agriculture UniversityUmair KhanNo ratings yet
- Operation Panel Setting Instruction ManualDocument16 pagesOperation Panel Setting Instruction ManualDinh NguyenNo ratings yet
- FC Vs FBDocument8 pagesFC Vs FBMiguel SanchesNo ratings yet
- Venn Diagrams and ProbabilityDocument19 pagesVenn Diagrams and ProbabilityAmosNo ratings yet
- Justification d1Document3 pagesJustification d1api-644892937No ratings yet
- Werewolf The Apocalypse Addendum 4102013Document70 pagesWerewolf The Apocalypse Addendum 4102013Kujo Red100% (1)
- Meaning, Types and Importance of Written CommunicationDocument12 pagesMeaning, Types and Importance of Written CommunicationHarsh GargNo ratings yet